Install Windows 2008 R2 NPS for RADIUS Authentication for Cisco Router Logins
A while back I documented a procedure to allow RADIUS Authentication for Cisco Router Logins. Shortly thereafter I included additional instructions on how to Set Up Windows 2003 IAS Server with RADIUS Authentication for Cisco Router Logins. This updated post will discuss the configuration of a Windows 2008 R2 server for Cisco router logins using RADIUS authentication. In my example I will install the Network Policy Server to support RADIUS on a Windows 2008 R2 domain controller and give router login access to an Active Directory domain user.
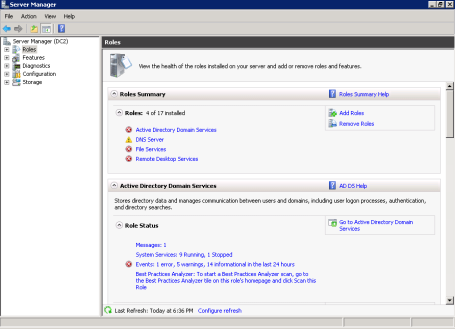
First go into Server Manager.
Highlight Roles on the left side, then in the Role Summary section click Add Roles on the far right.
When you reach the Select Server Roles screen, check Network Policy and Access Services. Click Next.
Check Network Policy Server only, then click Next. Then click Install and and confirm the install was successful.
Now go to Start > Admin Tools > Network Policy Server.
In the left pane open up Policies, then right click Network Policies and select New from the menu.
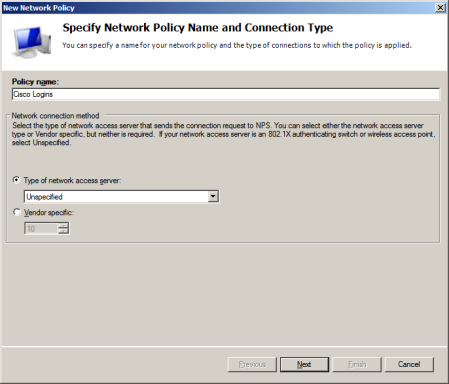
Type a name for the new login policy, leave the network access server type at Unspecified and click Next.
Click Add to add the conditions necessary for this network policy to be run.
We will specify that this policy is run for users in a specific Windows group, so highlight Windows Group and click Add.
Click Add Groups.
Type the name of the user group that you want to grant Cisco login access to. I will give this access to my Domain Admins. Click Check Names to verify, then click OK.
Click OK.








Seriously. Hands down one of the BEST guides out there. Thank you so much for getting me started!!!!!
I have a pretty much stright up setup of a Cisco WLC 4400.
Authenticatin using Radius.
After building my wn2008 R2 box, importing my config I am getting this error:
There is no domain controller available for domain xxxx.com.
Source:NPS Event ID: 4402
Any pointers?
Same config works fine on a 2008 system.
Great article, thanks for documenting this. I have a question though about the RADIUS client setup. I see the note about using wildcards but I’m a little confused. Do I need to setup a separate RADIUS client for each switch that I want to use NPS?
Hi Vin,
Yes, I believe you should be able to use a simple wildcard or a regular expression pattern to match multiple host names or IP addresses of your RADIUS clients. Unfortunately I did this writeup in a test environment which is no longer available and am using Windows 2003 IAS in production at the moment so I’m unable to test this functionality. More details on regex functions in NPS can be found below, in the middle they give an example of matching an IP address subnet range.
http://technet.microsoft.com/en-us/library/cc755272%28WS.10%29.aspx
Best wishes,
Aaron
Aaron,
Thanks for the quick response, and the link. I’ll check that out. I ended up exporting all the switch names and addresses from the previous RADIUS server and using a NETSH script to create the clients in the new server. I attempted to setup one of the switches with the appropriate IOS config and I see it’s attempt in the log, but it seems to be failing to authenticate. I’ll have to do a bit more work on it. Thanks again.
Vin
Brilliant blog, thanks for your time with this document.
Can you help me for when I do not want to use my W2008 servers as DC but as AAA only.
Jon
Hi Jon,
You should be able to configure a Win2008 server as a AAA server without it also being a DC. In fact in my environment I currently have a 2008 domain member server running NPS/AAA. I think the configuration procedure should basically be the same. Good luck!
Aaron
I have a pretty much stright up setup of a Cisco WLC 4400.
Authenticatin using Radius.
After building my wn2008 R2 box, importing my config I am getting this error:
There is no domain controller available for domain xxxx.com.
Source:NPS Event ID: 4402
Any pointers?
Same config works fine on a 2008 system
Hi Christian,
Are you saying that you exported your settings from 2008 NPS and imported them to 2008 R2? If so I haven’t used that functionality so I cannot confirm that it works without the error you are experiencing. Unfortunately I don’t have 2008 R2 NPS set up at the moment to try this out.
All the best,
Aaron
Yes, works just greta on the 2008 side..
when I run the same config on a R2 – I get that 4401 error.
Very strange and there is not much info out there.
Something I am concerned with, is where you say
“The Cisco IOS requires unencrypted authentication methods so select “Unencrypted authentication (PAP, SPAP)”. Click Next.”
I believe our settup needs to use the CHAP authentication, using an unencrypted authentication method is not a viable option for where I am working. How much would this document change, or the cisco router setup change, to use CHAP instead of unencrypted?
Thanks! Fantastic writeup!
Hello do you find solution for crypting authentification.
It will vert helpfull form me.
Thanks.
Thanks!
Works like a charm with OpenVPN too!
Great tutorial!! How would I set it up so I also have users log in with read only access?
You should be able to specify priv-lvl=7 if you need to.
Boa Tarde, amigo, qual seria o passo a passo para instalar o Radius no 2008 R2 para sincronizar autenticacao com um Lynksys 2500 da Cisco. Voces possui?
FYI, I used this guide to apply 802.1x authentication for a wireless connection and there was one crucial difference that took me awhile to sort out.
On the authentication configuration page there is no need to select “unencrypted authentication” but you do have to add “Protected EAP (PEAP)” under EAP types.
Im assuming this is because WPA Enterprise uses PEAP by default and, at least on the Cisco AP541N, there was no way to change authentication method.
Perhaps this could also be applied to the IOS config for wired 802.1x to make things a bit more secure?